We verify file checksums to ensure the file’s integrity, confirming no corruption or intentional modification has occurred. Anyone working with software distributions and versions, managing backups, or other files where data integrity is essential can use checksums to verify that they have the correct file.
A checksum is a value derived from a file’s content through a mathematical algorithm. It serves as the file’s fingerprint. Even the slightest change in the file’s content will give a completely different checksum, making checksums useful for detecting corruption or unauthorized modifications.
Common Checksum Algorithms
- MD5:
- Produces a 128-bit hash value, typically displayed as a 32-character hexadecimal number. The MD5 checksum algorithm is fast but has known vulnerabilities, making it less ideal for security-critical applications.
- SHA-1:
- Generates a 160-bit hash value, usually represented as a 40-character hexadecimal number. While more secure than MD5, SHA-1 is weak against modern cryptographic attacks.
- SHA-256:
- It belongs to the SHA-2 family and creates a 256-bit hash value, shown as a 64-character hexadecimal number. It offers a higher level of security and is commonly used today.
- SHA-384 and SHA-512:
- Part of the SHA-2 family, they create 384-bit and 512-bit hash values, respectively, offering a higher level of security.
Generating Checksums
MD5
To generate a checksum of a file using the MD5 algorithm, you can use the command md5sum.
md5sum <filename>For example, you can create a checksum of a txt or iso file using the command:
$ md5sum newfile.txtAnd you should receive a similar output.
8a4da784d5a4a40240070647e24ae3c8 newfile.txtNow, if you try to modify the txt file and generate the checksum again.
$ echo "adding new text" >> newfile.txt
$ md5sum newfile.txt
01d7b5d407a95eaa8ffeae996d9a9420 newfile.txtYou will notice that the checksum has changed.
SHA1
For generating SHA1 checksum, you can use the command:
sha1sum filenameFor example, you want the check the SHA-1 checksum of an file, you can do.
$ sha1sum somefile
c1f907c98e8dd422f4ad269afbd95cd773c90533 somefileSHA256, SHA384, SHA256:
The checksum algorithms from the SHA-2 family can be used with the commands sha256sum, sha384sum, and sha215sum.
$ sha256sum newfile.txt
20facfd89cc24ad86c0c867187c31460bfe05d5c6ed36cae7763da7eeed57d11 newfile.txt
$ sha384sum newfile.txt
3ab82cd318aa52c021a023d49ff6e654de21b7818b83223d5164013672a5ce3a4a5284f6833c4be132a6959927462cd8 newfile.txt
$ sha512sum newfile.txt
a114226d1cc3163ecfa6979a0556a65ec9161a7ebb2e5942aa447aa0d1097daa975586f134006e8dc4b51e21c50885c01b2fd43ac4e8278e72e1fe2597613c5e newfile.txtVerifying Checksums
- Manual Verification
To manually verify a checksum, generate the checksum of the file you want to verify using one of the commands above.
Then, compare this checksum with the known correct checksum value.
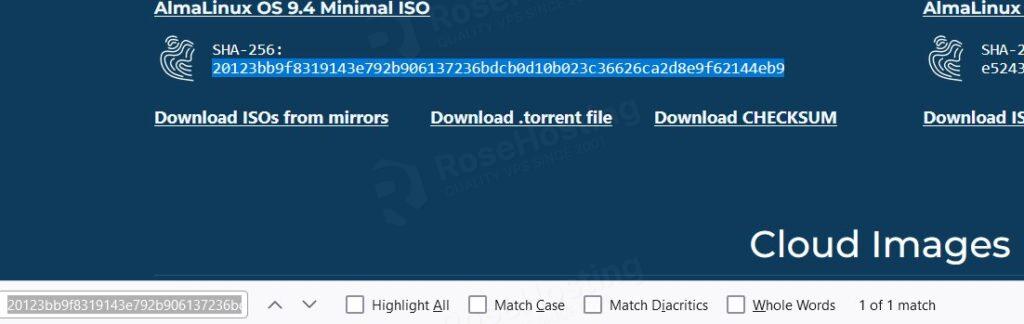
The most commonly used checksum algorithm today is SHA-256. If you are downloading a Linux distribution, you will always find the checksums on their website to make sure that the ISO image you downloaded is not corrupted or tampered with.
You can copy the generated checksum of the iso image you downloaded and use the CTRL-F find tool on your browser. Then, you can paste the generated checksum to check if the checksums match instead of comparing each checksum character.
- Using Checksum Files
If you have a file containing checksums (e.g., checksums.sha256), you can verify your files using:
$ sha256sum -c checksums.sha256The checksum file should list each checksum and the corresponding file. The -c flag will check each file and report if its checksum matches the recorded value.
$ md5sum -c checksums.md5In this command, -c tells md5sum to read checksums from a file and check the integrity of the files listed in it. Ensure that the checksum file follows the format checksum filename.
Conclusion
Checksums are a fundamental tool for ensuring file integrity. Using commands like md5sum, sha1sum, and sha256sum, you can efficiently generate and verify file checksums on Linux. More robust algorithms such as SHA-256, SHA-384, or SHA-512 will help you avoid any security concerns about data integrity compared to weaker checksum algorithms.
If you need help verifying file checksums, feel free to contact our server support. We’ll be happy to help.


